Pretend that you wake up and find out your bank account emptied, your social media accounts compromised, and your personal information exposed on the dark web.
Sadly, this nightmare unfolds for countless persons each year due to cyberattacks.
But what if there was a way to thwart these attacks before they even occur? That’s when security testing comes to life.
In this article, let’s discover what is security testing, its types, its fundamental principles, and invaluable best practices. Brace yourself for an immersive journey into the world of safeguarding digital landscapes.
What Is Security Testing?
This is security testing definition: Security testing assesses software vulnerabilities and gauges the impact of malevolent or unforeseen inputs on its functionality.
By subjecting systems to rigorous security testing, organizations obtain crucial evidence regarding the safety, reliability, and resilience of their software, ensuring that unauthorized inputs are not accepted.
Software security testing falls under the umbrella of non-functional testing, it’s different from the functional testing that evaluates the proper functioning of software features (“what” the software does).
In contrast, non-functional testing concentrates on verifying whether the application’s design and configuration are effective and secure.
Benefits Of Security Testing
Some benefits of security testing – an aspect of software testing include:
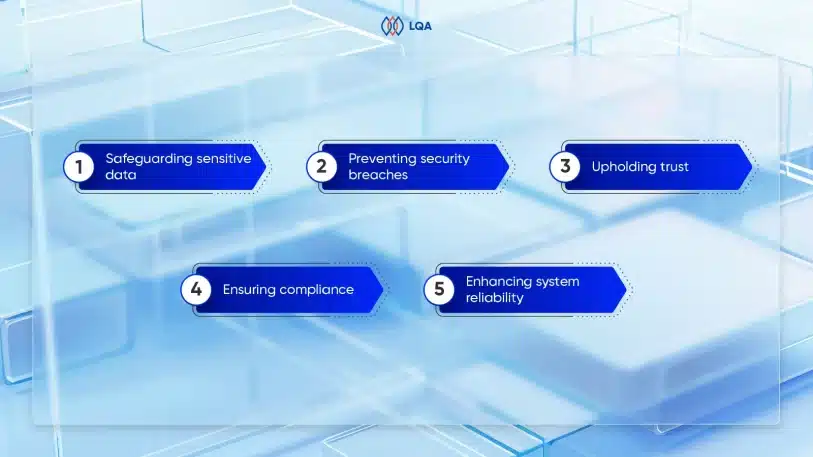
- Safeguarding sensitive data: Through meticulous evaluation, security testing shields confidential and sensitive information from unauthorized access, disclosure, or theft, providing a robust defense against potential breaches.
- Preventing security breaches: By unearthing vulnerabilities and weaknesses in the system, security testing acts as a proactive measure, thwarting security breaches and unauthorized intrusions that could compromise sensitive data’s sanctity.
- Upholding trust: Security testing plays a pivotal role in cultivating and preserving the trust of customers, clients, and users. By affirming the system’s security and safeguarding its information, it establishes a solid foundation of trustworthiness.
- Ensuring compliance: Various industries and organizations operate under stringent regulatory frameworks that mandate specific security measures. Security testing ensures adherence to these regulations, demonstrating compliance and mitigating potential risks and penalties.
- Enhancing system reliability: Security testing identifies and rectifies security weaknesses that may trigger system failures or crashes. By bolstering system resilience, it enhances overall reliability and minimizes disruptions.
In general, security testing assumes a crucial role in protecting sensitive data, upholding trust, meeting compliance requirements, and elevating system reliability.
Main Types Of Security Testing
Now, let’s embark on some security testing types in the realm of software testing. By skillfully combining these security testing methodologies, you can fortify your software, safeguarding it against potential cyber-attacks and ensuring a robust security posture.
- Vulnerability scanning
One of the prominent security testing types is vulnerability scanning. It entails scrutinizing your software for known vulnerabilities or weaknesses. This method employs automated security testing tools to uncover potential security flaws, such as outdated software components, weak passwords, or insecure network configurations. By identifying these weaknesses in advance, vulnerability scanning helps preemptively address security gaps before malicious actors can exploit them.
- Penetration testing
Or “pen testing,” penetration testing simulates real-world attacks on your software to uncover vulnerabilities and weaknesses. Ethical hackers or security professionals replicate the tactics employed by potential attackers, aiming to exploit security loopholes.
This security testing type focuses on scrutinizing authentication and authorization flaws, network configuration vulnerabilities (e.g., open ports, unencrypted traffic), and application logic flaws that arise from how your software handles user inputs or executes specific actions.
- Risk assessment
Risk assessment involves a meticulous examination of potential threats to your software, evaluating both their likelihood and potential negative impacts. This security testing approach encompasses analyzing the software’s architecture, design, and implementation to identify security risks, such as data breaches, denial-of-service (DoS) attacks, or malware and viruses.
Through risk assessment, you can better understand the vulnerabilities and receive recommendations to enhance your software’s security, empowering you to proactively tackle potential issues.
- Ethical hacking
Ethical hacking is similar to penetration testing as it involves emulating real-world attacks on your software. However, ethical hacking offers a distinct advantage by uncovering vulnerabilities that may elude other security testing approaches.
This security testing type includes assessing risks associated with phishing attacks, social engineering exploits, and physical security breaches. By engaging in ethical hacking, you can obtain a more comprehensive evaluation of your software’s security, including a broader spectrum of attack scenarios.
- Security scanning
Security scanning leverages automated tools to scrutinize software for potential security vulnerabilities. These tools for security testing can range from software-based to hardware-based scanners, proficient in detecting an extensive array of security issues.
Examples of such vulnerabilities include SQL injection, cross-site scripting (XSS), and buffer overflow attacks. Moreover, security scanning aids in adhering to industry standards and regulations governing software security.
While security scanning serves as a valuable tool for identifying potential security weaknesses, it should not be solely relied upon. This is because security scanning tools may not capture all software vulnerabilities and can produce false positives or negatives.
Therefore, you should complement security scanning with other impactful security testing methodology, such as penetration testing and risk assessment. By amalgamating these approaches, you can attain a holistic and comprehensive evaluation of your software’s security posture.
- Posture assessment
A meticulous evaluation of your software’s overall security posture is conducted through posture assessment. This form of security testing entails a thorough review of your software’s security policies and procedures, intending to identify any vulnerabilities or loopholes.
During the posture assessment, experienced security experts examine your access controls and software endpoints, providing valuable insights to help prevent targeted malicious attacks on your software.
The assessment catalyzes invaluable best practices in both operational and tactical aspects, ensuring that your organization’s security posture remains resilient and impervious to potential weaknesses, whether originating from IT service providers or third parties.

Moreover, posture assessment carries a review of your software’s incident response plan. This ensures the presence of appropriate procedures to effectively respond to security incidents.
Testing your ability to detect and respond to security breaches, and evaluating your capacity to recover from a security breach, are integral components of this assessment.
By conducting a comprehensive security posture assessment, you can proactively identify areas for improvement, fortify your defenses, and establish robust incident response mechanisms, thus safeguarding your software and mitigating potential security risks.
- Security auditing
Security auditing entails a comprehensive assessment of the design, implementation, and operational processes of your software to identify any gaps in your security controls.
When conducting security audits, you should initiate the process by clearly defining the scope, objective, and outlining the purpose, goals, and anticipated audit outcomes.
The next step involves collecting pertinent information about the software’s architecture, design, and implementation to pinpoint potential areas of weakness.
This can be achieved through a meticulous review of the software’s documentation, engaging in interviews with key stakeholders, and complementing the process with vulnerability scans and penetration testing.
Throughout the auditing process, identify and prioritize potential security weaknesses, vulnerabilities, and gaps in security controls. Based on the audit results, there will be some comprehensive recommendations to address the identified threats and enhance your security controls.
Security Testing Tools
Below are some software security testing tools
Static application security testing (SAST)
SAST tools perform an analysis of the source code in its static state. The primary objective of SAST is to detect potential vulnerabilities that can be exploited, offering a comprehensive report comprising detailed findings and corresponding recommendations.
By utilizing SAST, you can proactively identify and address various issues within the source code. These issues may include inadequate input validation, numerical errors, path traversals, and race conditions.
While SAST primarily focuses on source code analysis, you can apply it to compiled code, albeit with the use of binary analyzers.
Dynamic application security testing (DAST)
DAST tools specialize in scrutinizing applications while they are actively running. Their main objective is to identify potential vulnerabilities that can be exploited, employing a diverse array of attacks.
DAST tools frequently utilize fuzzing techniques, bombarding the application with numerous known invalid errors and unexpected test cases. This intensive approach means uncovering specific conditions in which the application may be susceptible to exploitation.
DAST checks cover a broad spectrum of components, including scripting, sessions, data injection, authentication, interfaces, responses, and requests. By running DAST assessments, you can gain insights into the security posture of these critical aspects, ensuring the robustness and resilience of your application.
Interactive application security testing (IAST)
IAST tools leverage a synergistic blend of static and dynamic testing methodologies, forming a powerful hybrid testing process. The primary objective is to determine whether known vulnerabilities present in the source code can be exploited during runtime.
By incorporating both static and dynamic analysis, IAST tools can minimize false positives, enhancing the accuracy of vulnerability detection.
IAST tools employ a combination of advanced attack scenarios, using pre-collected information about the data flow and application flow. Through iterative cycles of dynamic analysis, these tools continuously gather insights about the application’s behavior and response to various test cases.
This dynamic learning process enables the IAST tool to refine its understanding of the application’s vulnerabilities and may even generate new test cases to gain further insights.
By harnessing the capabilities of IAST tools, organizations can conduct comprehensive and intelligent testing, ensuring a more precise assessment of their application’s security posture during runtime.
Software composition analysis (SCA)
Software Component Analysis (SCA) is a cutting-edge technology designed to oversee and fortify open-source components in software systems. It empowers development teams to efficiently monitor and evaluate the utilization of open-source components in their projects.
SCA tools possess the capability to identify all pertinent components, including their supporting libraries, direct and indirect dependencies. Within each component, these tools can pinpoint vulnerabilities and recommend appropriate remediation measures.
By conducting thorough scanning, SCA generates a comprehensive Bill of Materials (BOM), presenting a detailed inventory of the software assets employed in the project.
Security Testing’s Key Principles
When engaging in any form of IT sec testing, whether it is web security testing, application security testing, data security testing, or others, you must adhere to the following fundamental principles.
- Confidentiality
Access control covers a set of regulations designed to ensure that information is accessible and handled solely by authorized entities. By implementing robust security measures, organizations can safeguard private and confidential information, preventing unauthorized access or exposure to inappropriate parties.
Essentially, access is restricted to authorized personnel, ensuring the confidentiality and integrity of sensitive data.
- Integrity
Data integrity revolves around upholding trust, consistency, and accuracy of information. Its primary objective is to facilitate the secure and accurate transfer of data from the sender to the intended receiver.
By implementing data integrity measures, organizations ensure that data remains unaltered by unauthorized entities, preserving its integrity throughout its lifecycle.
- Authentication
User authentication is a vital process that verifies individuals’ identity, establishing confidence in their access to systems or information. It ensures that users can trust the authenticity and reliability of information received from a recognized and trusted source.
- Authorization
Role-based authorization is a system where a user is granted specific access rights based on their designated role. This security testing principal ensures that users are authorized to perform tasks and access resources that align with their assigned roles and responsibilities.
- Availability
Information availability involves ensuring that data is readily accessible when needed by authorized individuals. This entails maintaining hardware infrastructure, promptly addressing hardware repairs, ensuring the smooth functioning of operating software, and safeguarding all data to prevent any disruptions in availability.
- Non – Repudiation
“Repudiation” means rejecting or denying something. Non-repudiation ensures that the creator or sender of a message or document cannot later deny its originality or authenticity, guaranteeing its undeniable origin and validity.
- CIA or AIC
Confidentiality, integrity, and availability (CIA) form the cornerstone of an information security model used to establish robust policies in organizations.
Test Scenarios for Security Testing
Here are a few illustrative software security test scenarios to provide you with a glimpse of potential test cases:
- Validate password encryption to ensure secure storage.
- Verify the system’s ability to block unauthorized users from accessing the application or system.
- Assess the handling of cookies and session timeouts in the application.
- Evaluate the prevention of browser back button functionality on financial websites.
Note that these are merely sample scenarios, and a comprehensive security testing strategy would have a broader range of test cases tailored to your specific requirements.
Approaches To Follow While Doing Security Testing
Security testing holds various methodologies, which are as follows:
Black Box Testing
Black box testing involves evaluating the security of a system from an external perspective, without knowledge of its internal workings or response generation processes.
The system is treated as an opaque entity, with only inputs and outputs observable. In certain cases, the tester intentionally disregards the internal structure, even if it’s understandable.
Black box testing ensures a clear separation between the tester and the code creator. It compels the tester to approach the software from an outsider’s standpoint, simulating how an attacker might perceive and exploit it.
The social and technical detachment between testing and software development empowers the tester to challenge the creator by manipulating the application in ways the developer may not have anticipated.
White Box Testing
White box testing involves the creation of test cases and conducting tests based on the software’s source code. Unlike black box or gray box testing (where the tester possesses limited knowledge about the code structure), in white box testing, the tester has a thorough understanding of the code’s structure.
This technique also means clear, transparent, or glass box testing due to its emphasis on code observability.
White box testing primarily focuses on examining the internal workings and software components of an application to assess its design and structure from within. Testing teams can employ this technique for conducting system, integration, and unit tests.
Gray Box Testing
Gray box testing performs a fusion of white box and black box testing methodologies.
While black box testing entails working with a test object of unknown internal structure and white box testing requires full knowledge of the application’s internal workings, gray box testing involves the tester having a partial understanding of the system’s internal structure.
Testers in gray box testing rely on a limited comprehension of the underlying architecture and code to design their tests. The test object is thus considered semi-transparent or “gray.”
This approach combines the targeted code examination of white box testing with the innovative and diverse approaches of black box testing, such as functional and regression testing. Gray box testers can simultaneously evaluate both the software’s user interface and internal mechanisms.
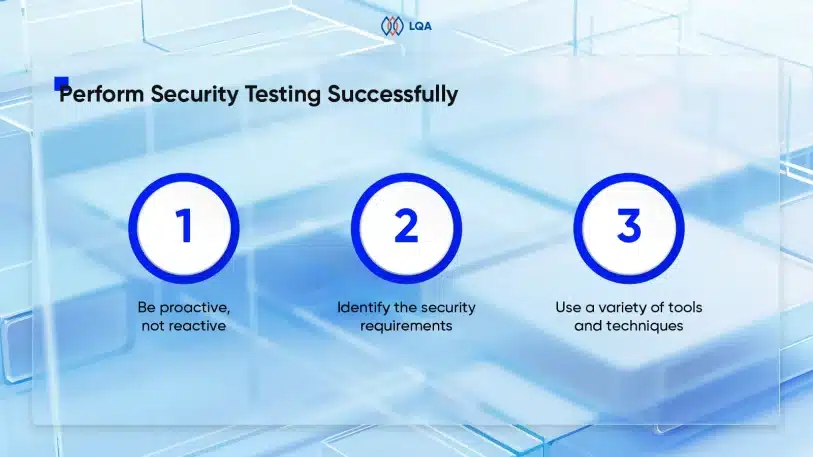
How To Perform Security Testing Successfully?
Implementing effective computer security testing is essential for early detection and mitigation of vulnerabilities in your software development lifecycle. To ensure precise and accurate security testing in software testing, you should follow the best practices that guarantee a comprehensive, efficient, and effective process.
The following key practices can assist you in achieving these objectives:
Be proactive, not reactive
Take a proactive approach to security testing and avoid waiting until an attack occur. Regularly conduct comprehensive testing of your systems to quickly identify and resolve vulnerabilities before they can be exploited by attackers.
Use a range of automated security testing tools to scan your systems periodically, ensuring thorough vulnerability assessments. If needed, don’t hesitate to seek assistance from specialized vendors that can conduct penetration tests on your systems.
Adopt an attacker’s mindset and consider the most probable methods through which your systems could be breached. By understanding these potential vulnerabilities, you can concentrate your efforts on fortifying those specific areas.
Identify the security requirements
Before initiating security testing, establish the security requirements specific to your software. This ensures that the testing process focuses on the most critical security concerns.
To identify these requirements, begin by reviewing pertinent security policies and regulatory standards applicable to your software. These may include industry-specific regulations like HIPAA or PCI DSS, as well as broader security standards such as ISO 27001 or NIST SP 800-53.
By adhering to these guidelines, you can effectively align your security testing with the relevant industry and regulatory frameworks.
Proceed by evaluating the software’s risk profile to ascertain the potential consequences and likelihood of various security threats and attacks. This evaluation may involve undertaking a threat modeling exercise or a comprehensive risk assessment to identify and prioritize security risks effectively.
Subsequently, define precise security requirements that align with the identified risks and relevant regulations and standards. These requirements should possess clarity, measurability, and testability.
They should comprehensively address different dimensions of security, including confidentiality, integrity, availability, and non-repudiation. By establishing such requirements, you can ensure a robust and focused approach to safeguarding your software.
Use a variety of tools and techniques
To obtain a comprehensive understanding of your system’s security posture, you should employ a diverse range of testing methods. Relying on a single approach is insufficient to capture all vulnerabilities.
To identify security weaknesses in your application, you can use a combination of SAST (Static Application Security Testing), DAST (Dynamic Application Security Testing), and penetration testing.
SAST tools scrutinize source code for vulnerabilities, while DAST tools scan running applications to uncover potential weaknesses. Additionally, penetration testers simulate attacks on your application, helping to find and address security vulnerabilities through a proactive approach.
By leveraging these varied testing methods, you can enhance your systems’ overall security.
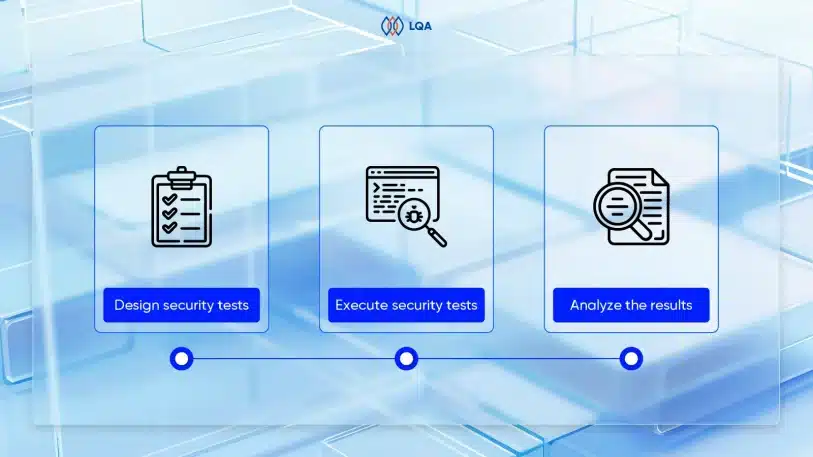
Design security tests
Aligning with the established security requirements, formulate security tests focus on uncovering previously unidentified vulnerabilities and weaknesses. To create these tests, identify the specific types of security tests pertinent to your software, as previously discussed. Subsequently, determine the scope and objectives for each test.
Construct test cases and scenarios that replicate real-world attacks. Consider the potential consequences and likelihood of each vulnerability, and prioritize testing endeavors accordingly based on risk assessment.
Conclude by documenting the test plan and sharing it with stakeholders for feedback and approval. Incorporate revisions to the plan based on received feedback, ensuring its readiness for execution.
Execute security tests
During the execution of security tests, don’t forget to meticulously adhere to the devised plan to ensure precise and thorough testing. Take diligent note of any encountered issues throughout the testing phase, and document them for subsequent analysis.
Employ a systematic approach to guarantee all tests completion, leaving no vulnerabilities overlooked.
To streamline the workflow during security testing, contemplate the utilization of automated security testing tools. These tools facilitate the testing process and generate comprehensive reports on identified vulnerabilities and weaknesses. By leveraging such tools, you can save time and maintain consistency in test execution.
Furthermore, involve your development teams and security experts in the testing process to ensure comprehensive coverage of potential issues. Their expertise and collaboration will contribute to addressing any identified concerns effectively.
Analyze the results
A thorough analysis of security test results is a vital aspect of the software security testing process. This entails carefully checking the collected testing data to find out any potential security concerns that require attention.
To carry out an effective analysis of security test results, you should document the testing outcomes with precision and comprehensiveness. This documentation serves as a foundation for in-depth examination and evaluation of the identified security issues.
Comprehensive documentation should encompass extensive information regarding the conducted tests, obtained results, and any discovered issues or vulnerabilities throughout the testing phase.
This documentation plays a vital role in assessing the severity and prioritization of each identified concern, as well as devising a robust plan for their resolution.
In addition, actively seek feedback from industry professionals, as their expertise and insights can contribute to the development of effective strategies for addressing the identified vulnerabilities. Collaborating with these experts ensures a well-informed and strategic approach to resolving the security issues at hand.
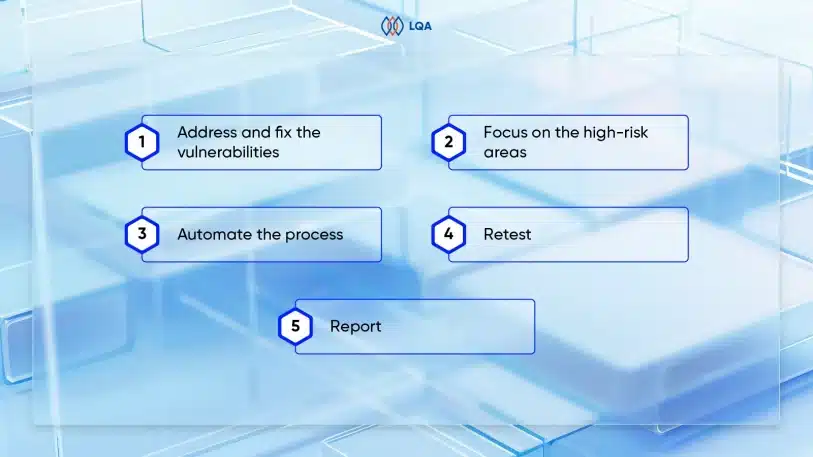
Address and fix the vulnerabilities
Upon identification of potential vulnerabilities, you should promptly address them to establish robust software security. When addressing these vulnerabilities, you should determine prioritization by their severity and potential impact on the software’s security.
Critical vulnerabilities demand immediate attention, followed by those of medium and low severity. Developing a comprehensive remediation plan that have all identified vulnerabilities and includes a timeline for completion is quite important.
Furthermore, ensure the use of secure coding practices while resolving vulnerabilities. Implement measures like input validation and output sanitization to prevent similar vulnerabilities in the future.
By adopting these practices, you protect the software’s resilience against potential security risks.
Focus on the high-risk areas
Vulnerabilities are various, with certain ones posing greater risks to your systems. Hence, you should concentrate your testing endeavors on higher risk level areas.
Using a risk assessment tool can address these high-risk areas within your systems. Armed with this knowledge, you can allocate your efforts accordingly and prioritize testing in those specific areas.
However, remember to not overlook the low-risk areas. Attackers can exploit even vulnerabilities with lower risk levels if they are skillfully combined. Therefore, comprehensive testing should include all areas, ensuring a thorough evaluation of potential vulnerabilities.
Automate the process
Efficiently automating security testing is vital, considering the time and cost implications associated with manual security testing.
One effective approach is to leverage CI/CD pipelines, which automate the entire testing process. These pipelines facilitate the seamless building, testing, and deployment of software applications.
By integrating security testing tools into your CI/CD pipeline, you can automatically scan both your code and running applications for potential vulnerabilities. This automation significantly streamlines the testing process, enhancing efficiency and effectiveness.
Retest
After addressing the vulnerabilities, you should conduct retesting the software to verify the effectiveness of the fixes. This step will prevent the inadvertent creation of new vulnerabilities during the remediation process.
During the retesting phase, adhere to the established testing plan and procedures from the previous testing phase. Whenever possible, maintain consistency by employing the same testing tool.
It is worth noting that retesting should not be limited to software fixes alone; perform it after any modifications or updates to the software. By conducting thorough retesting, you ensure the continued security and stability of the software after changes or improvements.
Report
Communicate the results of security testing to stakeholders, ensuring their awareness of any potential security concerns, and the corresponding measures taken to mitigate them.
To create impactful security testing reports, employ clear and concise language that avoids excessive technical jargon.
In addition, you should also add a comprehensive summary of findings in the report. This summary provides an overview of the testing process, highlights key findings, and offers recommendations for remediation.
This summary serves as a valuable starting point for further discussions and decision-making among stakeholders.
Incorporating supporting evidence such as screenshots, log files, and vulnerability reports enhances the credibility of the report and enables stakeholders to grasp the severity of vulnerabilities.
These tangible pieces of evidence bolster the report’s credibility and aid stakeholders in comprehending the significance of identified vulnerabilities.
Lastly, ensure the inclusion of actionable recommendations that stakeholders can implement as part of their security measures. These practical suggestions empower stakeholders to take concrete steps in detecting the highlighted security concerns.
FAQ
What is security testing?
Security testing involves the meticulous identification and elimination of software weaknesses that could potentially ruin a company’s infrastructure system. By proactively addressing these vulnerabilities, we can brace the software’s resilience against attacks.
How is security testing different from software testing?
Distinguishing itself from other software testing practices, security testing focuses on uncovering vulnerabilities that hackers can exploit to infiltrate systems. Unlike other testing methodologies that primarily target functional deficiencies, security testing specifically aims to safeguard against unauthorized access and potential breaches.
Can security testing be automated?
Absolutely, automation is indeed possible. A diverse range of tools exists specifically designed to scan and detect vulnerabilities in code, web applications, and networks.
These tools play a significant role in enhancing system and application security by swiftly identifying and resolving vulnerabilities, thereby thwarting potential exploitation by attackers.
Nevertheless, you should acknowledge that automated tests cannot entirely replace manual testing. Manual testing identifies and addresses vulnerabilities that automated tools may overlook.
The combination of both automated and manual testing ensures an extensive approach to security testing, minimizing the risk of undetected vulnerabilities.
> Read more:
- Automation Testing vs. Manual Testing: Which Is The Cost-Effective Solution For Your Firm?
- From Manual to Automation Testing: Why Even Bother?
- How to Transition from Manual to Automation Testing: 6 Crucial Steps
Difference between QA and security testing
QA testing primarily focuses on verifying that software adheres to its functional requirements and performs as intended. QA testers approach software testing from the perspective of an average user, ensuring its usability and meeting user expectations.
On the other hand, security testing focuses on proactively identifying and resolving vulnerabilities in software that could be exploited by malicious attackers. Security testers adopt the mindset of a potential adversary, simulating attack scenarios to uncover weaknesses and fortify the software’s security.
QA testing cannot substitute for security testing. Even if software successfully passes all QA tests, it may still harbor undetected security vulnerabilities.
Therefore, conducting thorough security testing is essential to identify and rectify these vulnerabilities before the software is released to the public, ensuring a robust and secure product.
Conclusion
In the realm of software engineering, safeguarding data is important, making system security testing indispensable. Among the various testing practices, security testing takes precedence as it guarantees the confidentiality of personal information.
In this testing approach, one assumes the role of an attacker, meticulously examining the system to unveil any security vulnerabilities.
However, conducting such tests manually consumes substantial resources in terms of time, finances, and personnel. Therefore, transitioning to automated testing is a prudent way forward.
In case you want to find an efficient software testing service provider, don’t hesitate to contact us:
- Website:https://www.lotus-qa.com/
- Tel: (+84) 24-6660-7474
- Mail: [email protected]