Cybersecurity is the art of safeguarding networks, devices, and data from unauthorized access or misuse, ensuring information remains confidential, intact, and accessible.
While cybersecurity isn’t a new concept, it’s on the cusp of significant changes in 2024. Cyber threats are not only increasing in frequency but also growing more sophisticated, fueled by the widespread adoption of artificial intelligence (AI), machine learning (ML), and IoT. This calls for fresh protection strategies from stakeholders.
Here are 8 cybersecurity trends for 2024 that your organization should take note of.
 Increased Use of AI and ML
Increased Use of AI and ML
AI in cyber threat detection
As the frequency of modern security threats continues to surge, relying solely on human intervention for cybersecurity is no longer sufficient. Consequently, more and more businesses are leveraging the power of AI and ML to fortify their security frameworks.
The benefits are tangible: organizations that experienced data breaches but had fully integrated AI technology saved an average of $1.76 million in 2023.
Looking ahead to 2024, AI and ML will take on even greater significance in the realm of cybersecurity.
AI has already proven instrumental in crafting automated security protocols, deciphering natural language, recognizing faces, and swiftly identifying potential threats.
Its sophisticated data analysis capabilities are becoming indispensable for preempting and detecting new cyber threats early on. By continuously analyzing risks, AI tools can promptly flag suspicious user behavior, abnormal login attempts, and irregular network activities.
In addition, the advent of AI-driven security bots seems imminent, programmed to autonomously detect and thwart cyber threats, fostering a more proactive approach to network security.
Meanwhile, ML algorithms are constantly evolving to improve their ability to identify and counteract emerging threats, thereby bolstering defensive measures with time. It’s foreseeable that ML will progress to autonomously adapt and refine cybersecurity protocols, reducing the need for manual updates.
AI-powered cyberattacks
On the flip side of AI’s potential for reinforcing threat detection is its exploitation by cybercriminals.
Hackers are increasingly harnessing AI to automate their attacks, employing tactics such as data poisoning and model stealing. Examples of such malicious activities include
- automated phishing attempts,
- malevolent chatbots,
- the utilization of adversarial ML algorithms to disrupt operations and tamper with data integrity.
With the aid of AI, criminals can devise advanced malware and sophisticated attack strategies. They train AI models with pilfered data and then adopt various AI tools to dissect stolen data and extract sensitive information. This makes it much easier for cybercriminals and hackers to successfully carry out data breaches and ransomware attacks.
Furthermore, the advent of generative AI (GenAI) allows attackers to execute campaigns at scale, targeting a vast array of individuals with highly personalized and convincing emails. Access to personal information such as names, organizations, job titles, departments, or even health data helps attackers tailor their attacks with unprecedented precision, posing a significant challenge to cybersecurity professionals.
The Rise in Cloud Security Threats
The next cybersecurity threat trend is cloud vulnerability. The widespread adoption of remote work, especially post-pandemic, has accelerated the need for cloud-based services and infrastructure, bringing along security concerns for organizations. Indeed, approximately 20% of data breaches within companies are attributed to remote workers utilizing cloud-based platforms.
Alongside data breaches, businesses grapple with various network security trends and cloud security challenges, including:
- ensuring compliance with regulations across different jurisdictions
- seeking adequate IT expertise to manage the complexities of cloud computing
- addressing challenges in cloud migration
- managing an increased number of potential entry points for cyber attackers
- tackling insider threats, whether accidental or deliberate, stemming from unauthorized remote access, weak passwords, insecure networks, and misuse of personal devices.
According to Deloitte’s annual cybersecurity threat report, Software-as-a-Service (SaaS) and cloud-based storage services were the most targeted cloud environments in 2023, accounting for 39% and 36% of attacks, respectively. Deloitte’s Cyber Threat Intelligence (CTI) also revealed specific threat vectors in the cloud, including unmanaged attack surfaces, human error, and misconfigurations.
One effective strategy to counter this cyber attack trend is Zero Trust. One of the prominent advantages of this approach lies in its efficacy in mitigating insider threats and thwarting lateral movement of attackers within a network.
At its core, Zero Trust operates on the principle of “never trust, always verify”.
In a zero-trust model, every access request is treated as a potential threat, regardless of its source or network. This approach requires stringent identity verification, tight access controls, and continuous monitoring of network activities.
Typically, once implementing Zero Trust, your organization has to take into account numerous cybersecurity aspects, from user authentication, and endpoint security, to the principle of least privilege access.
Growing Importance of IoT Security
The Internet of Things (IoT) refers to physical objects equipped with sensors and actuators that connect to computer systems through wired or wireless networks, enabling digital monitoring or control of the physical world.
Common examples of IoT devices include fitness trackers, smart refrigerators, smartwatches, and voice assistants like Amazon Echo and Google Home. It’s projected that by 2026, there will be 64 billion IoT devices worldwide.
However, the growing number of IoT devices poses numerous security challenges.
To be specific, the diversity and widespread usage of these devices make them attractive targets for cyberattacks, and their interconnected nature can lead to extensive vulnerabilities.
The proliferation of these devices also expands what’s known as the cyber-attack surface – the potential entry points for malicious actors. In addition, unlike laptops and smartphones, most IoT devices have limited processing and storage capabilities, making it difficult to implement conventional security measures like firewalls and antivirus software.
In response, 2024 will witness a concerted effort to bolster IoT security through various means.
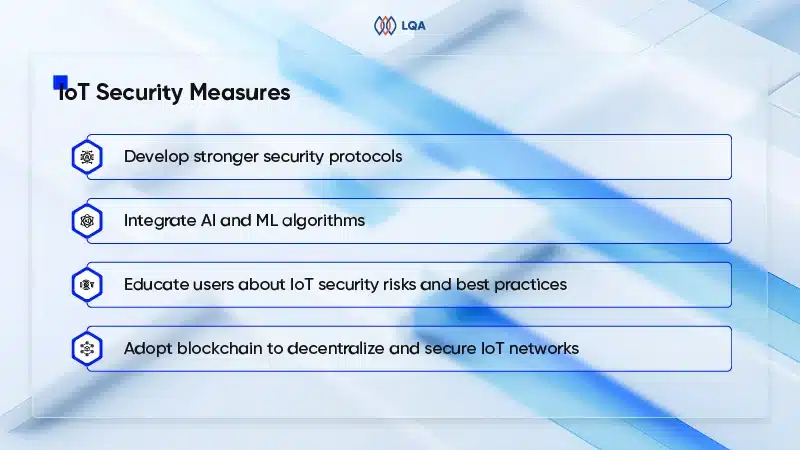
One significant advancement will be the development of stronger, standardized security protocols for IoT devices, potentially including universal encryption standards and mandatory security certifications.
Plus, there’ll be a growing focus on integrating AI and ML algorithms and blockchain technology into IoT systems to detect unusual patterns indicative of breaches and enable rapid threat response.
An increased emphasis on educating users about IoT security risks and best practices is also expected to lead the trend in 2024 within organizations.
At LQA, we specialize in delivering top-notch embedded software testing services globally. Our expert testers meticulously examine sensor functionality, network security systems, and other aspects of IoT devices, ensuring compliance with robust and standardized security protocols. Whether it’s sensor testing, network testing, or industrial protocol testing, rest assured, we have the expertise to ensure the secure and seamless operation of your organization’s IoT system.
Remote Working Cybersecurity Risks
Remote work continues to reshape the business and cybersecurity landscape in 2024. According to Upwork, over 35 million Americans are expected to work remotely by the end of 2025, marking an 87% increase from pre-pandemic levels. However, this trend comes with its own set of cybersecurity risks.
Chances are most home offices lack the robust security measures found in centralized offices, such as secure firewalls, routers, and managed access controls. As a result, adapting to remote work setups may lead to less stringent security measures, giving cybercriminals opportunities to exploit vulnerabilities.
Besides, many employees use personal devices for work-related tasks and this blurring of personal and professional boundaries heightens the risk of sensitive information being compromised.
Hence, it’s crucial for organizations to prioritize addressing the security challenges posed by distributed workforces. This involves:
- constantly identifying and mitigating emerging security vulnerabilities,
- updating systems,
- implementing security controls,
- ensuring proper monitoring and documentation.
We also highly recommend your business invest in Identity and Access Management Tools (IAM) to further mitigate risks and improve operational management. With IAM solutions, companies can easily analyze user activities, streamline secure sign-in processes based on corporate norms, and prompt users for additional authentication when needed.
Enhanced Focus on Mobile Security
In 2024, the growing reliance on mobile devices for remote work, financial transactions, personal communication, etc. is forecasted to make them prime targets for cyber threats.
In general, mobile threats encompass:
- specialized spyware targeting encrypted messaging apps
- exploitation of critical device security vulnerabilities by criminals
- mobile malware capable of executing various attacks such as Distributed Denial of Service (DDoS), SMS spam, and data theft

Standing among the latest cybersecurity technology trends, mobile cybersecurity covers a wide array of components, including back-end, cloud security, network security, and the expanding network of interconnected devices, known as the Internet of Things (IoT), such as wearables and automotive devices. That’s why there’s no one-size-fits-all approach to safeguarding apps in insecure environments; rather, it involves implementing multiple layers of security to boost overall protection. Some security experts are even integrating mobile software security with hardware-based solutions to strengthen data storage security.
To address mobile security concerns fully, businesses can leverage LQA’s premium secure mobile application testing services. Our rigorous testing not only takes place before app releases but also on a continuous basis, assuring compliance with functional, performance, and security standards to elevate your overall software quality and user satisfaction.
Blockchain and Cybersecurity
Blockchain technology is gaining increasing recognition for its potential to greatly enhance cybersecurity practices. Essentially, blockchain is a decentralized ledger system known for its built-in security features such as immutability, transparency, and resistance to tampering. These attributes make it an attractive solution for safeguarding digital transactions and shielding data from emerging cyber threats.
One significant way blockchain is bolstering cybersecurity is by preventing data tampering. Once data is recorded on a blockchain, it becomes practically impossible to alter without network consensus, thus preventing hackers’ attempts at manipulation. This feature proves particularly valuable for securing sensitive information like personal identities, financial transactions, and critical infrastructure data.
Blockchain can also be leveraged to develop more secure and decentralized identity management systems. By storing identity data on a blockchain, individuals and organizations gain greater control over information access, thereby minimizing the risks of identity theft and fraud.
Furthermore, blockchain is poised to play a more pivotal role in securing IoT devices. Integration of blockchain into IoT networks enables each device to function as a secure, independent node, strengthening the entire network against attacks that exploit centralized security vulnerabilities.
The adoption of blockchain-based smart contracts is also anticipated to rise, facilitating automation and security in digital agreements. These self-executing contracts offer enhanced security in various online transactions, guaranteeing compliance and reducing breach risks.
The Evolution of Ransomware Attacks
Ransomware is a form of malicious software (malware) that threatens to block access to data or computer systems, usually by encrypting them, until a ransom fee is paid to the attacker.
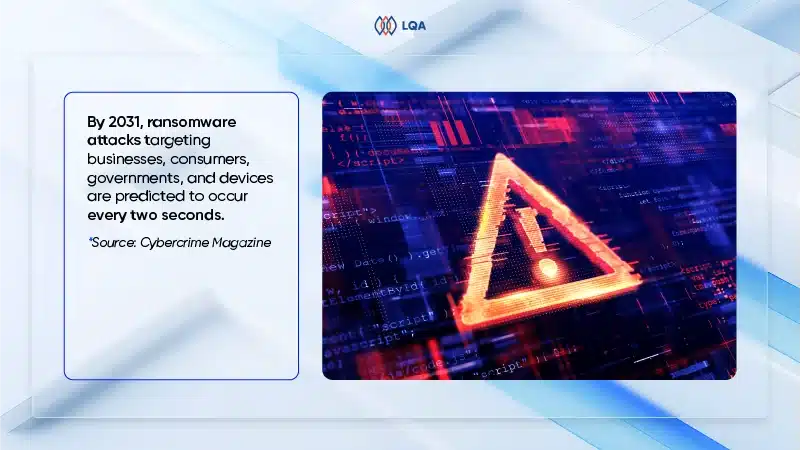
According to a US government report, there are over 4,000 ransomware attacks daily. Cybercrime Magazine even reported that in 2021, a targeted ransomware attack occurred approximately every 11 seconds, excluding attacks on individuals. It’s projected that ransomware attacks on businesses, consumers, governments, and devices will happen every two seconds by 2031.
And these losses exceeded $1 billion in 2023, as reported by the Professional Insurance Agents Western Alliance, underscoring the urgent need for adaptation in cybersecurity technologies.
However, a huge roadblock is that ransomware tactics have rapidly evolved over the past decade, transitioning from locker malware that blocked system access to current methods involving data encryption and exfiltration. These techniques are successful because decrypting data without the hackers’ decryption key is extremely challenging, if not impossible. Even when the ransom is paid, nearly a quarter of companies, as per the 2023 Ransomware Trends report, still don’t regain access to their data; and around 34% of encrypted data remains unrecoverable.
On top of that, ransomware attackers are becoming increasingly sophisticated in their phishing tactics, leveraging machine learning and dark web collaboration, while often demanding payment in cryptocurrencies, making tracing particularly difficult.
In the near future, we expect more ransomware attacks targeting organizations that lack robust security testing measures, including a concerning trend known as Ransomware as a Service (RaaS).
In this model, cybercriminals provide ransomware tools and infrastructure to other malicious actors, who then execute attacks.
The emergence of RaaS demands comprehensive and proactive cybersecurity testing measures, along with close collaboration between public and private sectors.
Regulatory Compliance as a Discipline
Last but not least, an important cybersecurity future trend to watch is the rising significance of regulatory compliance.
Generally, regulations related to cybersecurity can be categorized into two main types: data protection regulations and cybersecurity regulations. While these requirements may overlap, they each have distinct focuses. One crucial aspect to differentiate between them is that the theft or accidental release of consumer data often leads to administrative penalties and other financial repercussions.
Regarding cybersecurity regulations, they outline the most basic security standards for products, software, and networks. A few examples of such regulations are:
- The EU’s NIS2 cybersecurity law
- New York’s NYDFS cybersecurity regulations
- The UK Product Security and Telecommunications Infrastructure regime
- Payment Card Industry Data Security Standard (PCI DSS)
As for data privacy, as it impacts nearly all aspects of an organization, non-compliance with regulations can lead to fines, negative publicity, and erosion of consumer trust.
As a consequence, businesses are increasingly focusing on hiring data privacy officers and implementing measures like role-based access control, multi-factor authentication, encryption of data in transit and at rest, network segmentation, and external assessments to identify areas for improvement.
FAQs about Top Trends in Cybersecurity in 2024
What are the most common cybersecurity threats today?
Among the most prevalent cybersecurity threats are phishing attacks, ransomware, different types of malware like Trojans and viruses, insider threats, and Distributed Denial of Service (DDoS) attacks.
How can individuals and businesses enhance their protection?
Individuals and businesses can bolster their cybersecurity by regularly updating their software, using strong and unique passwords, implementing multi-factor authentication, educating themselves on cybersecurity practices, and investing in reliable antivirus and anti-malware software.
What are the impacts of emerging technologies on future cybersecurity?
Emerging technologies like AI and IoT offer promising opportunities but also pose significant challenges for the future of cybersecurity. While AI can strengthen threat detection and response, it also introduces new risks exploited by cybercriminals. Similarly, IoT devices bring in vulnerabilities that malicious actors can exploit. To effectively combat the latest cybersecurity threats, future cybersecurity strategies must adapt to incorporate these technologies into comprehensive defense mechanisms.
Final Thoughts about Cybersecurity Industry Trends
As we’ve discussed the top 2024 emerging trends in cybersecurity above, it’s evident that our digital world is rapidly changing, from the rise of cloud-based services to the emergence of new IoT devices. This evolution brings fresh challenges and underscores the need for robust defenses.
To stay secure amidst growing threats, 2024 calls for a modern cyber-defense approach that remains adaptable to ever-changing trends of cybersecurity. Both individuals and organizations should assess their current digital footprint and strategize ways to reduce the risk of attacks – both now and in the future.
- Website: https://www.lotus-qa.com/
- Tel: (+84) 24-6660-7474
- Mail: [email protected]
- Fanpage: https://www.linkedin.com/company/lqa/




