What Is Penetration Testing? | A Comprehensive Guide
Understanding your strengths, vulnerabilities, and where your team should allocate time is crucial in the realm of cybersecurity. However, determining these factors and prioritizing tasks can be challenging. So, conducting penetration testing is a highly effective approach to gaining clarity.
Penetration testing is a solid basis for any security team. It excels at pinpointing what to focus on and proposing initiatives for your team’s future endeavors. So, what exactly is pen testing, and why is it so important? The following article will provide further insights.
What is Penetration Testing?
A penetration test (or pentest), is a sanctioned simulation of an attack carried out on a computer system to assess its security. Penetration testers employ identical tools, methods, and procedures as actual attackers to discover and illustrate the detrimental effects of system vulnerabilities.
These tests typically simulate diverse attack types that pose potential risks to a business. They evaluate the system’s ability to resist attacks from authorized and unauthorized sources, as well as various system roles. With appropriate parameters, a pen test can delve into any system facet.
Why is Penetration Testing Important?
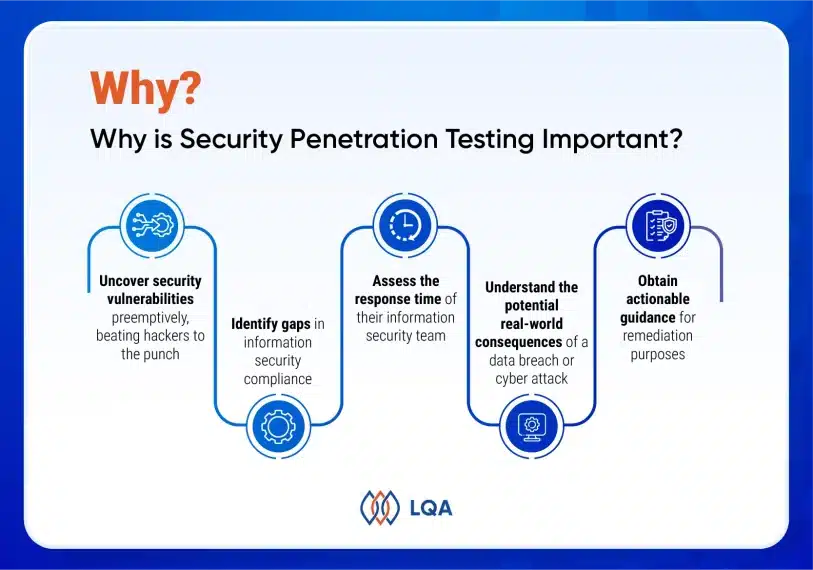
A penetration test holds a strong significance in ensuring network security. This testing methodology enables businesses to accomplish the following objectives:
- Uncover security vulnerabilities preemptively, beating hackers to the punch.
- Identify gaps in information security compliance.
- Assess the response time of the information security team, gauging how quickly to detect breaches and minimize the impact.
- Understand the potential real-world consequences of a data breach or cyber attack.
- Obtain actionable guidance for remediation purposes.
Penetration testing empowers security experts to methodically assess the security of multi-tier network architectures, custom applications, web services, and other IT components.
Penatration testing services and tools provide swift visibility into high-risk areas, letting businesses build security budgeting.
Comprehensive testing of an organization’s entire IT system, a web app or a mobile app is crucial for safeguarding critical data from cyber hackers and enhancing the IT department’s responsiveness during potential attacks.
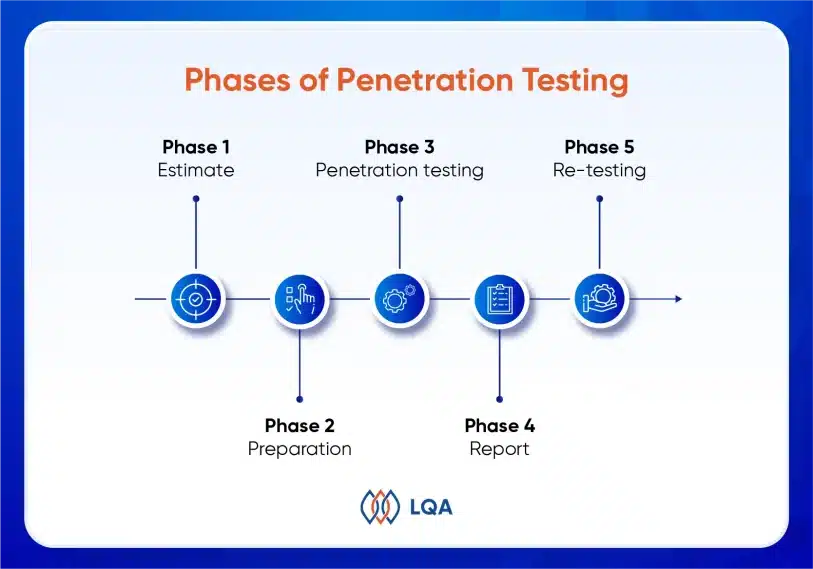
5 Phases of Penetration Testing
Penetration testers replicate the tactics employed by determined adversaries. At LQA, we adhere to a comprehensive plan that encompasses the following penetration testing process:
Phase 1 – Estimation
In the first pen testing process, we need to understand the exact number of items in scope, such as
- HTTP requests in web application and API,
- screens & main functions in Android / iOS application,
- server and network devices,
- IP addresses in systems.
Then, we build a plan based on the function severity. The ranking on a scale of A to S will be used as a criterion for customers to select items to test from the estimate list.
Phase 2 – Preparation
In this phase, we need to prepare some things before testing, including:
- Web application information: Site name, host, system, cloud services, penetration testing type (remote, onsite), period time, environment testing.
- Access restriction: Restricting access with IP address, basic authentication, we also need some special configured access settings.
- Account information: Multiple permission settings, multiple accounts (username and password).
- Various process: Assessment of functions associated with various processes and external systems.
- Validation: Confirm other important information before testing.
Phase 3 – Penetration testing
In this phase, LQA’s testing team will:
- Schedule penetration testing
- Implement manual and automated testing
- Analyze and evaluate detected vulnerability
- Analyze and evaluate the case of threats and impacts when the vulnerability is exploited
Phase 4 – Report
In the report phase, we will:
- Send daily quick report for high-risk vulnerability detected.
- Write a summary and technical report, then deliver the final report.
Phase 5 – Re-testing
In the last phase, LQA’s testing team will re-test the vulnerabilities after remediating programs.
After completing a successful pen-test, an ethical hacker collaborates with the target organization’s information security team to share their findings.
Typically, these findings are categorized with severity ratings, enabling the prioritization of remediation efforts. Issues with the highest ratings are addressed first to ensure effective resolution.
A business uses these findings as a foundation for conducting additional investigations, assessments, and remediation to enhance its security posture.
At this stage, decision-makers and stakeholders become actively involved, and the IT or security team establishes deadlines to ensure prompt resolution of all identified security issues.
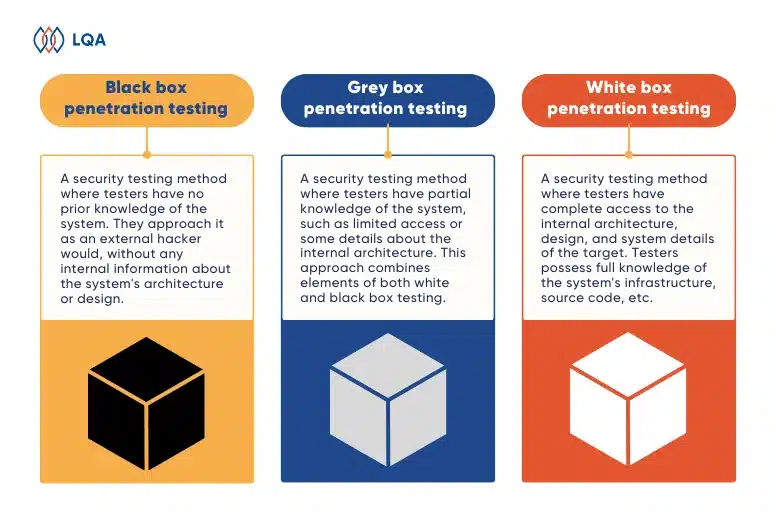
Pen Testing Approaches
Penetration testing includes a trio of primary approaches, each equipping pen testers with specific levels of information required to execute their attacks effectively.
- White box testing: In white box testing, the customer furnishes comprehensive system information, including accounts at various access levels. This ensures that the testing expert can band encompass system’s functionalities.
- Black box testing: Black box penetration testing is a form of behavioral and functional testing in which testers are intentionally kept unaware of the system’s inner workings. Organizations commonly engage ethical hackers for black box testing, as it simulates real-world attacks and provides insights into the system’s vulnerabilities.
- Gray box testing: Gray box testing combines white box and black box testing techniques. Testers are granted limited knowledge of the system, including low-level credentials, logical flow charts, and network maps. The primary objective of gray box testing is to identify potential code and functionality issues in the system.
>> Read more:
Best software testing methods to ensure top-quality applications
What Should Good Penetration Testing Include?
To ensure a robust the pen test engagement, business should conduct a thorough assessment of an organization’s attack surface.
This assessment aims to identify all conceivable entry points into the network, encompassing unsecured ports, unpatched vulnerabilities, misconfigured systems, and weak passwords.
By addressing these critical aspects, organizations can fortify their defenses against potential security breaches.
After the identification of potential entry points, the penetration tester proceeds to exploit them to gain network access. Once inside, pentesters meticulously examine the network for sensitive information, including customer data, financial records, and proprietary company secrets.
Furthermore, the tester endeavors to escalate privileges to obtain complete control over the network.
How Often Should Pen Tests Be Performed?
The frequency of conducting penetration testing varies based on several factors, yet most security experts advise performing it at least annually. This regular assessment aids in the detection of emerging vulnerabilities, including zero-day threats, ensuring proactive mitigation measures can be promptly implemented.
When planning the schedule for penetration testing, organizations should focus on the following key considerations:
- Cyber-attack risks: Organizations with increased exposure to potential financial and reputational damage, should prioritize regular security testing to proactively prevent cyber-attacks.
- Budget: The frequency of pen testing should align with the available budget and its flexibility. Larger companies may have the resources to conduct annual tests, while smaller businesses might opt for biennial assessments due to budget constraints.
- Regulatory requirements: Certain industries, such as banking and healthcare, have specific regulations mandating regular penetration testing. Compliance with these regulations should guide the frequency and timing of security assessments in those organizations.
Apart from regular scheduled penetration testing, organizations should also consider conducting security tests in response to the following aspects:
- Incorporating new network infrastructure or appliances into the network.
- Implementing upgrades to existing applications and equipment.
- Installing security patches.
- Establishing new office locations.
- Modifying end-user policies.
What are The Best Penetration Testing Tools?
Penetration testers employ a diverse range of tools to execute reconnaissance, identify vulnerabilities, and streamline essential aspects of the penetration testing process. Here are several widely used tools:

- Specialized operating systems: Penetration testers rely on specialized operating systems tailored to penetration testing and ethical hacking.
Among these, Kali Linux stands out as the preferred choice. This open-source Linux distribution comes equipped with an array of built-in pen testing tools, including Nmap, Wireshark, and Metasploit.
- Credential-cracking tools: In the pursuit of uncovering passwords, penetration testers leverage credential-cracking tools. These software applications employ various techniques such as encryption-breaking or launching brute-force attacks.
By using bots or scripts, these tools systematically generate and test potential passwords until a successful match is found. Prominent examples encompass Medusa, Hydra, Hashcat, and John the Ripper.
- Port scanners: These tools enable pen testers to remotely examine devices for open and accessible ports, which can serve as potential entry points into a network. While Nmap remains the most popular port scanner, other commonly used options include Masscan and ZMap.
- Vulnerability scanners: These scanning tools are designed to identify known vulnerabilities in systems, enabling pen testers to swiftly pinpoint potential weaknesses and entryways into a target. Notable examples of vulnerability scanners include Nessus, Core Impact, and Netsparker.
Web vulnerability scanners include a specialized category of tools within the broader realm of vulnerability scanning. These scanners specifically evaluate web applications and websites to identify potential vulnerabilities. Notable examples in this domain include Burp Suite and OWASP’s Zed Attack Proxy (ZAP).
- Packet analyzers: Also referred to as packet sniffers, empower penetration testers to analyze network traffic by capturing and examining individual packets.
These tools provide insights into the origin, destination, and, in some cases, content of transmitted data. Prominent packet analyzers include Wireshark and tcpdump, widely recognized for their effectiveness in this domain.
- Metasploit: On the other hand, serves as a comprehensive penetration testing framework encompassing a multitude of functionalities. Its most significant attribute lies in its ability to automate cyber attacks.
Equipped with a comprehensive library of prewritten exploit codes and payloads, Metasploit empowers penetration testers to select an exploit, assign a payload to deliver to the target system, and delegate the remaining tasks to the framework itself.
Penetration Testing Case Study
Below are two outstanding LQA’s penetration testing case studies you can refer to:
SaaS penetration testing

Overview
The product is a SaaS service software system that uses the Microsoft Azure cloud based on business management.
Its features aim at the user experience and business development system for small and medium enterprises.
Project information
- Country: USA
- Domain: ERP
- Framework: .NET, Vue
- Tools Involved: Burp Suite Professional
What we did
Our objective was to assess the security of the web applications by conducting a thorough penetration test aligned with the OWASP Top 10. This helped us identify and mitigate vulnerabilities to enhance the security posture.
Findings
- Privilege Escalation
- Account Takeover
- Stored XSS
- File Upload Vulnerabilities
- Information Leakage
Achievements
We found 12 vulnerabilities, fixed 100% of severe issues, and did 1400 APIs tested.
Dental clinic management system penetration testing
Overview
Our client has a dental clinic management system to make appointments, bookings, check exam results, invoicing, etc.
However, their system, which was built a decade ago on outdated PHP, lacked optimized performance, sustainability, and security. So, they needed an experienced vendor to upgrade their technology stack to ensure easier maintenance and future development.
Project information
- Country: France
- Domain: Healthcare
- Framework: NodeJS, React
- Tools Involved: Burp Suite Professional
What we did
Based on our client’s requirements, we needed to assess the security of the web applications by conducting a thorough penetration test aligned with the OWASP Top 10. This helped to identify and mitigate vulnerabilities to enhance its security posture.
Findings
- SQL Injection
- Access Control Issues
- Weak Authentication Mechanism
- Information Leakage
Achievements
We found 8 vulnerabilities, fixed 100% severe issues, and did 390 APIs tested.
FAQ
How often should I run a penetration testing?
The optimal frequency of conducting penetration tests varies for each company, contingent upon factors such as the nature of its operations and its appeal to potential attackers.
In the case of highly sensitive activities, you should conduct penetration tests regularly, ideally several times per year. This approach ensures that the latest attack methods are thoroughly tested and safeguards against emerging threats.
For activities of lower sensitivity, you should perform a penetration test for each new version release or whenever significant features are added. This targeted approach focuses on assessing the security of specific updates or additions, thereby maintaining an adequate level of protection.
By tailoring the frequency of penetration tests to the unique characteristics and risk profile of each company, organizations can proactively address potential vulnerabilities and bolster their overall security posture.
I don’t have sensitive data, why would I be attacked?
No website is immune to cyberattacks, even those that may not possess sensitive data.
Hackers can have varied motivations, ranging from honing their skills and knowledge, to exploiting compromised servers for hosting malicious websites, generating profits, or even simply seeking amusement.
Among the most frequently targeted websites are those built on the WordPress platform. These sites often face automated attacks on a massive scale, targeting tens of thousands of websites.
The victims of such attacks are not specifically singled out, but rather fall victim to the widespread and indiscriminate nature of these automated campaigns.
How much does a pentest cost?
The required time and budget for testing depend on the scope and level of thoroughness desired.
If comprehensive and exhaustive testing is sought, it is natural if you expect a longer duration and, consequently, a higher financial investment.
You can contact LQA to have further discussion and detailed quotation.
What is the most important step in a penetration testing?
The estimation phase holds significant importance in a penetration test as it serves as the foundation for gathering crucial information about the target. This stage is particularly critical since having a comprehensive understanding of the target significantly simplifies the gaining access process.
What are the risks of penetration testing?
Improperly executed penetration tests can potentially result in significant damage, leading to adverse consequences. For instance, servers may experience crashes, essential data might be corrupted or compromised, and the overall aftermath could be a criminal hack.
>> Read more:
- How to create a test plan? components, steps and template
- Cybersecurity testing: definition, different types, and comprehensive guide
- Top 10 software testing companies in the world in 2023
- How to choose an automation testing services provider
Conclusion
In light of the continuously advancing and sophisticated nature of cyberattacks, we can’t overstate the significance of regular penetration testing in organizations. These tests play a vital role in identifying vulnerabilities, patching security loopholes, and validating the effectiveness of cyber controls.
By conducting pen testing methodology, organizations adopt a proactive approach to fortifying their infrastructure, software applications, and even their personnel against potential threats.
This proactive stance motivates the development of robust and continuous security measures that can adapt to the ever-changing cyber threat landscape, ensuring the organization remains resilient in the face of evolving challenges.
Leveraging the expertise of LQA, companies can establish a comprehensive defense against both recognized and unforeseen threats. By enlisting their support, you can proactively prevent, identify, and mitigate potential risks.
If you are eager to implement penetration testing, we encourage you to reach out to LQA. Contact us today for further discussion!
- Website: https://www.lotus-qa.com/
- Tel: (+84) 24-6660-7474
- Mail: [email protected]
- Fanpage: https://www.linkedin.com/company/lqa/