Penetration testing, or pen testing, also called ‘ethical hacking’, in the world of software testing is a cybersecurity practice that involves simulating cyberattacks on computer systems, networks, or applications to identify and address security vulnerabilities.
Black box penetration testing, together with gray box penetration testing and white box penetration testing, makes up the three major methods in the field of penetration test.
In this article, LQA will give you a comprehensive guide to black box penetration testing and its difference from the other two.
What is black box penetration testing?
Black box penetration testing definition
Black box testing in penetration testing is a security assessment where testers, with no prior knowledge of the system, simulate real-world attacks to identify vulnerabilities from an external perspective.
The goal of black box penetration testing is to assess the system’s resilience to external threats and provide recommendations for improvement.
 Key characteristics of black box testing
Key characteristics of black box testing
- Limited knowledge: Testers have little to no knowledge of the internal workings, code, or architecture of the system being tested.
- External perspective: Testing is conducted from an external viewpoint, simulating how an external attacker with no insider information would approach the system.
- Objective evaluation: Testing is conducted from an external viewpoint, assessing an app’s resistance to external threats without bias from internal knowledge.
- Real-world simulation: The goal is to simulate real-world attacks to identify vulnerabilities and weaknesses that could be exploited by external threats.
When your organization might need this type of pen test?
With the above characteristics of back box penetration testing, there are various scenarios when your organization might need this type of pen test. Common scenarios are:
- Early vulnerability detection: Use this type of pen test when your business wants to unveil vulnerabilities at the initial stages of the software development life cycle (SDLC) and address issues before they escalate into significant security concerns.
- Compliance & regulatory obligations: When industry regulations or compliance standards mandate regular security assessments, black box testing can help meet these requirements by providing an unbiased evaluation.
- Real-world simulation: A black box approach helps assess your application, infrastructure, or network in a setting that closely mirrors a real-life attack scenario.
- Third-party vendor assessment: Before onboarding a new third-party service or vendor, conducting black box testing helps ensure the security of their external-facing systems.
Black-box vs. Gray-box vs. White-box Penetration Testing
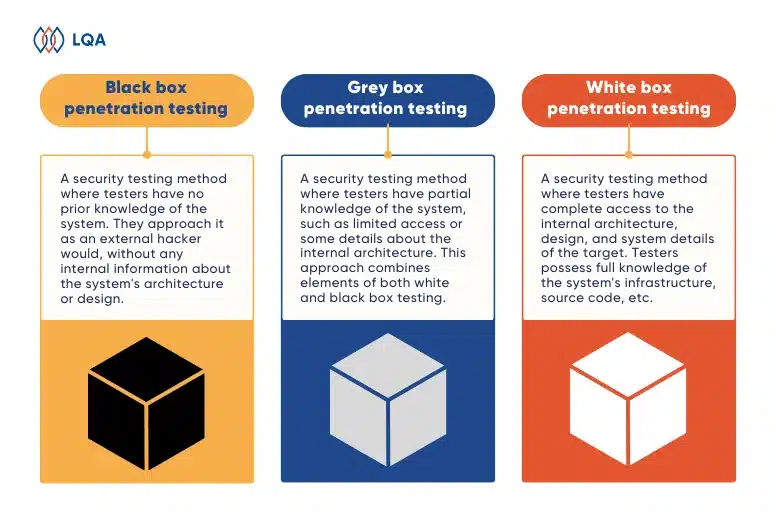
You may want to take a wider look at black box, white box. and gray box testing before digging into these software testing methods in the niche of cybersecurity testing.
| Aspect | Black box testing | White box testing | Grey box testing |
| Knowledge of internal details | Minimal to none | Comprehensive (full access) | Partial (limited internal information) |
| Testing perspective | External (simulates real attacks) | Internal (assumes insider knowledge) | Blend of external and limited internal |
| Realism | High (simulates external threats) | Moderate (assumes some insider knowledge) | Balanced realism and efficiency |
| Pre-engagement information | Limited preparation required | Detailed internal information needed | Moderate preparation required |
| Focus | External threats | Internal and external threats | Both internal and external threats |
| Use cases | External security assessment | Application and internal network testing | Third-party vendor assessment, balancing realism and efficiency |
| Efficiency | Quick start | May consume more time as detailed internal knowledge required | Balanced efficiency and realism |
Advantages and disadvantages of black box penetration testing
Below are the most common advantages and disadvantages of black box pen test during a penetration testing engagement.
Advantages of black box penetration testing
- Realistic testing: Assess your application, infrastructure, or network in a setting that closely mirrors a real-life attack scenario.
- Unbiased evaluation: Testing is conducted from an external viewpoint, eliminating insider bias from internal knowledge.
- Quick start: Back box testing doesn’t require testers to learn about the internal structure of software, hence allowing a quick start.
- Cost saving: It may be cheaper to conduct a black box penetration test compared to other pen testing types, as it doesn’t require much time and resources needed for preparation.
- Reduced chances of overlooking external vulnerabilities: As penetration testers don’t have prior access to the system blueprints and processes, the chances of testers focusing on a specific set of external vulnerabilities and missing out on others are often low.
Disadvantages of black box penetration testing
- Limited understanding of internal controls: The testing team has restricted knowledge of the internal workings, potentially missing nuanced vulnerabilities that require internal context.
- Overlooking internal vulnerabilities: The external focus may result in missing certain internal vulnerabilities that could be identified with more internal knowledge.
- Lack of context: While efficient, the quick start may come at the cost of lacking context for a more nuanced evaluation of internal security measures.
Common Black-box Penetration Testing Techniques
 Enumeration
Enumeration
Enumeration is about listing test targets for comprehensive testing.
Enumeration involves identifying and listing all possible test targets, such as IP addresses, services, and applications, to create a comprehensive inventory for testing.
It helps testers understand the scope of the system and potential points of entry.
Full port scanning
Full port scanning is crucial for mapping out the entire attack surface and discovering hidden services that might be overlooked with selective scanning.
Full port scanning is a specific scanning technique that involves checking all possible ports on a target system for open and closed statuses. This comprehensive approach helps identify services running on each port, providing insights into potential entry points for attackers.
Fuzzing
Fuzzing, or fuzz tests, is an automated testing technique that injects malformed or random inputs into an application that the application is not designed to handle.
The purpose of fuzz tests is to detect crashes, errors, memory leaks, and different behavior than expected.
Exploratory testing
Exploratory testing is when you perform tests with minimal predefined test plans and test cases and without an expectation or specific outcome.
Exploratory testing uses a dynamic and unscripted approach with the idea of letting the outcomes of one test guide the others.
This particularly works in black-box penetration testing, in which testers have no idea about the internal workings of the system.
Vulnerability scanning
Vulnerability scanning is an automated technique that systematically identifies and evaluates potential vulnerabilities within the target system, network, or application.
In vulnerability scanning, testers leverage automated tools to scan for common vulnerabilities in the target’s external-facing components.
This type of black-box pen test provides a quick and efficient way to identify potential security issues, such as outdated software, misconfigurations, or known vulnerabilities.
Exploitation
Exploitation involves attempting to exploit identified vulnerabilities to gain unauthorized access or compromise the target’s security.
During exploitation, testers simulate real-world attacks, crafting malicious requests to exploit weaknesses in the system’s defenses. This process demonstrates the potential impact of successful exploitation and assesses the overall security resilience of the target
Black Box Penetration Testing Steps
A black box pen test process often goes through 8 steps as below.
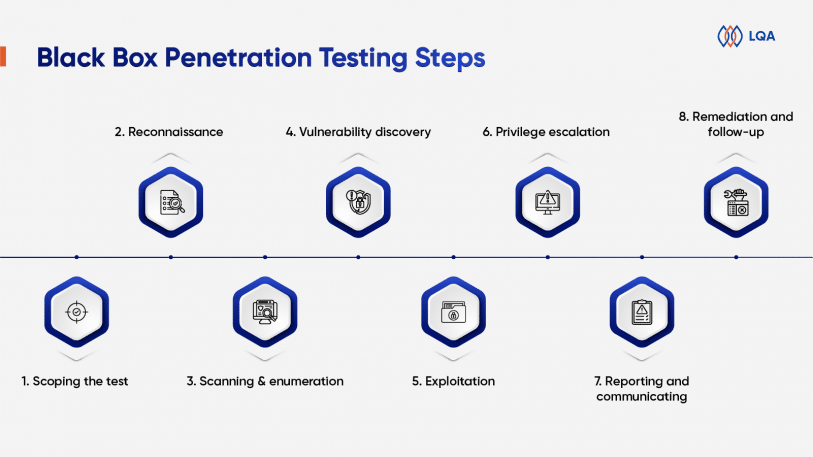 1. Scoping the test
1. Scoping the test
In this stage of the penetration test, the team defines the scope of the test, outlining the specific systems, applications, or networks to assess.
They also establish rules of engagement, setting guidelines and limitations for the testing process.
2. Reconnaissance
Reconnaissance involves gathering information about the target system, typically publicly known information such as domain names, employee information, IP addresses, and network configurations.
The purpose of the reconnaissance step is to collect publicly known information about the target system to lay the foundation for subsequent testing phases.
3. Scanning & enumeration
Post reconnaissance, testers conduct a further step to identify additional technical data about the target system, such as types of running software, operating system details, connected systems, user accounts, and user roles.
The step aims to enhance the tester’s understanding and inform subsequent testing actions.
4. Vulnerability discovery
Utilize gathered information in previous steps, testers identify public vulnerabilities in the public components target systems and networks. This involves searching for known common vulnerabilities and exposures (CVEs) in system components, versions, or third-party applications.
5. Exploitation
At this stage, pen testers craft malicious requests or use social engineering techniques to exploit the identified vulnerabilities actively. The objective is to penetrate the system efficiently and navigate to the core.
6. Privilege escalation
After gaining initial access, testers attempt to escalate privileges to achieve complete control over the system and database.
This stage is crucial for assessing the potential impact of a successful attack and understanding the extent of compromised access.
7. Reporting and communicating
After completing black box penetration testing, the test team comprehensively documents findings, outlining discovered vulnerabilities, exploitation methods, and potential risks.
Then, the test team presents a clear and actionable report, providing insights for stakeholders on areas of concern and recommended remediation steps.
8. Remediation and follow-up
At the remediation stage, the test team and stakeholders coordinate to fix and address identified vulnerabilities.
Follow-up assessments should be conducted to verify the effectiveness of remediation efforts and ensure a more secure environment.
How To Choose The Right Pen Test Provider?
There are cases when a company lacks internal capabilities for implementing penetration tests and seeks outsourcing. In such instances, choosing the right provider is crucial to delivering the expected outcomes.
Here are LQA’s suggestions for choosing the right pen test vendor:
- Prioritize providers with expertise in your industry and familiarity with your specific systems and technologies.
- Look for a provider willing to customize their testing approach to address your company’s unique security concerns and priorities.
- Consider the vendor’s price-to-quality commitment, which assesses the cost of the services in relation to the value offered.
- Investigate the provider’s reputation by reviewing testimonials, case studies, and online feedback from previous clients.
- Emphasize the provider’s commitment to ethical hacking practices and integrity in handling sensitive information to ensure a trustworthy collaboration.
- Your vendor should also communicate clearly, detailing their methodologies, findings, and recommendations in a way that is easily understandable for your team.
Black Box Penetration Testing by LQA
Enhancing cybersecurity testing involves engaging a specialized security firm to assess your business’s vulnerabilities and deliver a detailed report with recommended solutions, a crucial step in preventing cyber attacks.
Having more than 7 years of experience, and as the pioneering independent software testing company in Vietnam, LQA stands out as a prominent software quality and security assurance firm, offering a complete range of penetration testing services to fortify businesses against security threats.
Alongside black box penetration testing services, LQA provides comprehensive software testing services including white box, black box, web application, mobile application, API, manual, and automation testing services.
At LQA, we maintain up-to-date expertise on the latest threats, attacks, and vulnerabilities, employing industry-leading tools to conduct comprehensive penetration tests.
Frequently Asked Questions about Black Box Penetration Testing
1. What is the timeline for black-box penetration testing?
The timeline for black-box penetration testing can vary based on factors such as the scope, complexity of the target environment, and the specific testing objectives.
Below is a typical timeline for black box penetration testing:
- Planning: 1 – 2 weeks
- Target system’s information gathering: 1 – 2 weeks
- Execution: 1 – 2 weeks
- Reporting: 1 week
- Communicate reports: 1 day
2. What is more costly: black box or white box penetration testing?
The cost comparison between black box and white box penetration testing is context-dependent. For example:
- In case you develop the system in-house and have an internal test team who deeply understands the internal structure of the system, you can quickly kick off white box testing with minimal preparation. On the contrary, black box testing demands additional time and resources for information gathering, potentially costing more.
- In another scenario, where a legacy system lacks documentation and internal teams lack technical insights, white box testing may become more expensive. This is because it necessitates a substantial investment in understanding the system, while black box testing can commence more promptly.
3. What is the difference between gray-box and black-box penetration testing?
Black box penetration testing requires no knowledge of the internal workings of the target system. Meanwhile, gray box penetration testing requires partial knowledge of the internal workings of the target system.
Final Notes On Black Box Penetration Testing
Black box penetration testing is among the three major pen test approaches: black box, grey box, and white box. Among them, the black box method serves as an independent and objective method, simulating real-world cyber threats without prior knowledge of the system’s internal workings.
If you are looking for experts in conducting black box testing services, don’t hesitate to contact LQA’s security testing team.
